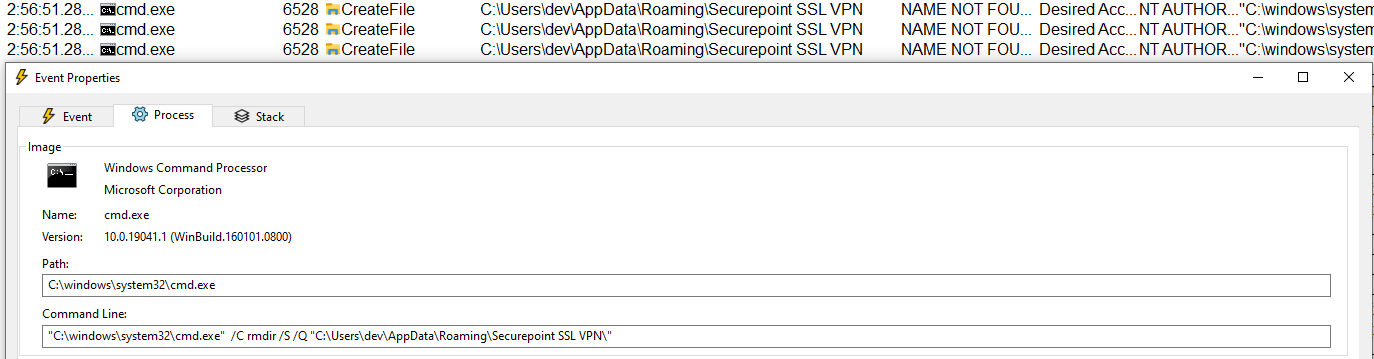
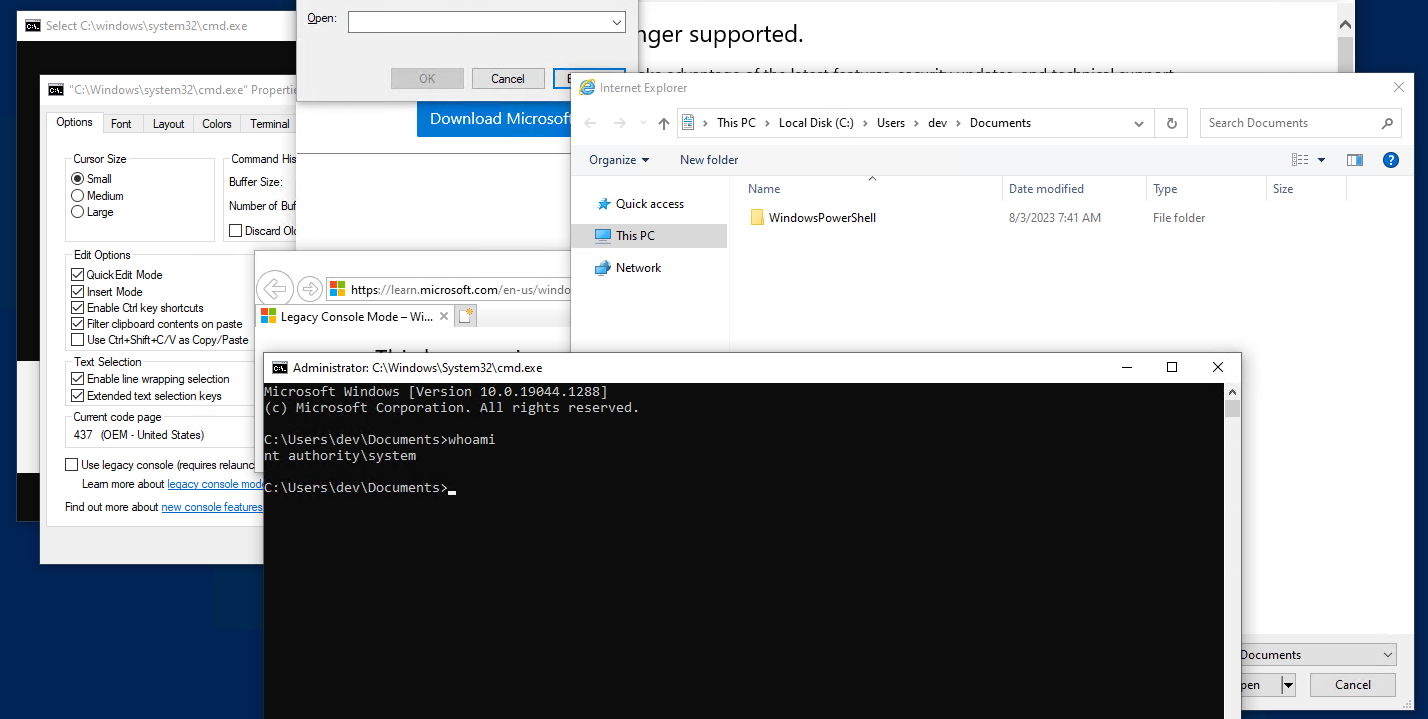
| Product | Securepoint SSL VPN Installer |
| Vendor | Securepoint GmbH |
| Affected Versions | <= 2.0.39 |
| Tested Versions | 2.0.39 |
| Subject | Improper Privilege Management - CWE-269 |
| Risk Level | Medium |
| Solution Status | fixed |
| Manufacturer Notification | Aug 8 2023 |
| Solution Date | Aug 25 2023 |
| Public Disclosure | Oct 13 2023 |
| CVE Reference | CVE-2023-47101 |
| Author | Matthias Zöllner, Cyvisory Group GmbH |